Learn how to setup Cisco DUO MFA that you will be able to use on your homelab to secure your access
In a previous article, I explained how you can centralize your authentication using Authentik. You can now access your applications using a unique identifier.
But what about ssh connection ? It would be great to be able to have a unique second factor for either my web applications and my ssh logins. It is where Duo comes in the game.
⚠️ You can also use the radius endpoint for Unix authentication of Authentik but I wanted that user management remain local to servers
I also have to tell that Cisco Duo remain totally free for 10 users and you don’t have to provide any payment method.
You have a mobile application which support Push notifications and you can use any FIDO 2 key.
And of course it provide a pam authentication module to setup MFA on linux servers.
Configure your tenant
Subscribe to DUO
Create an account on Duo sign up page
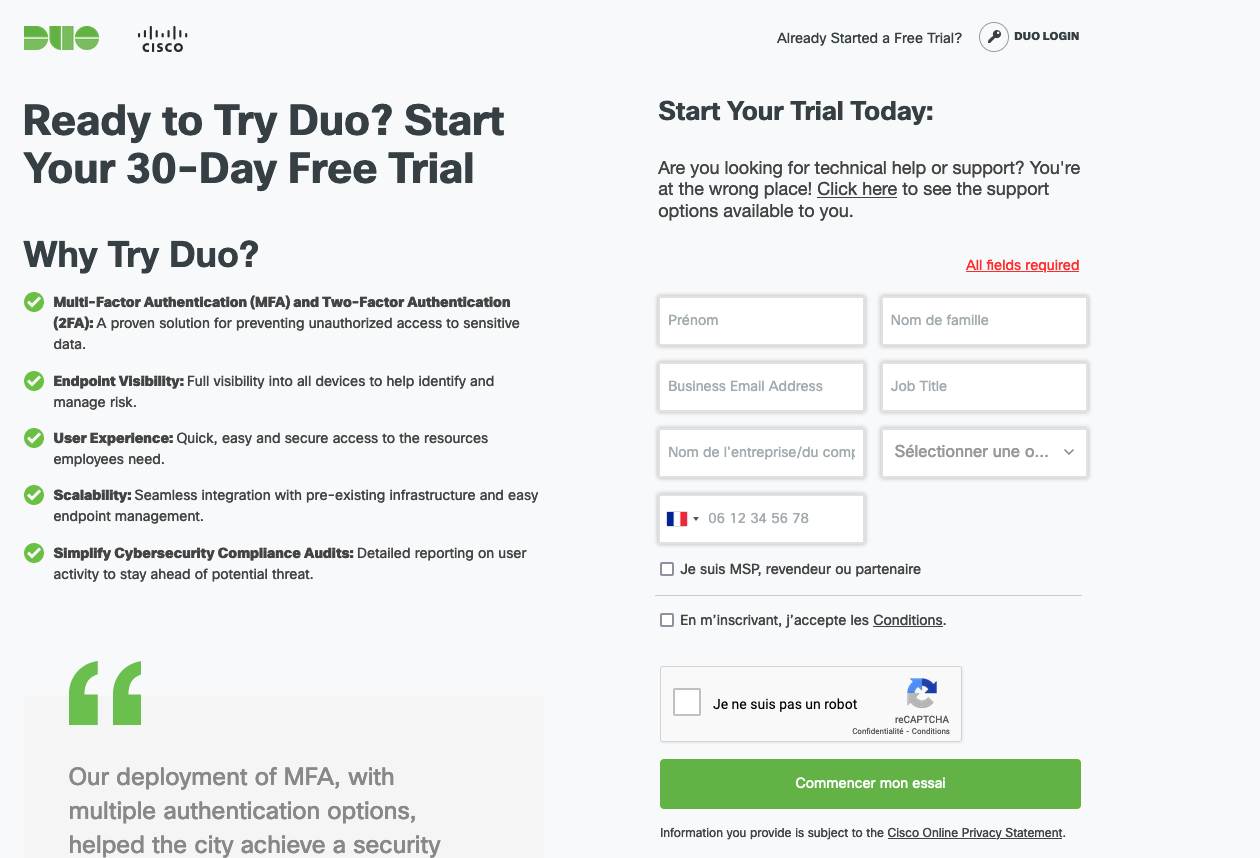
Complete the process and setup your admin account that will get access to the Duo admin console.
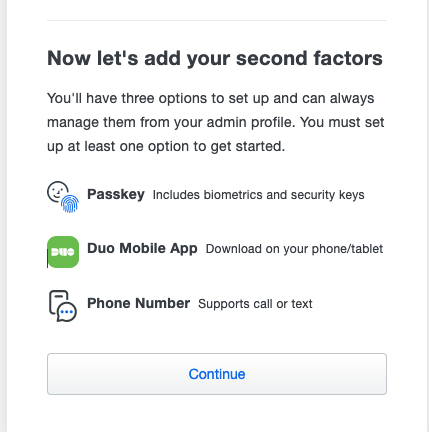
Complete your login and you will reach the Duo admin console.
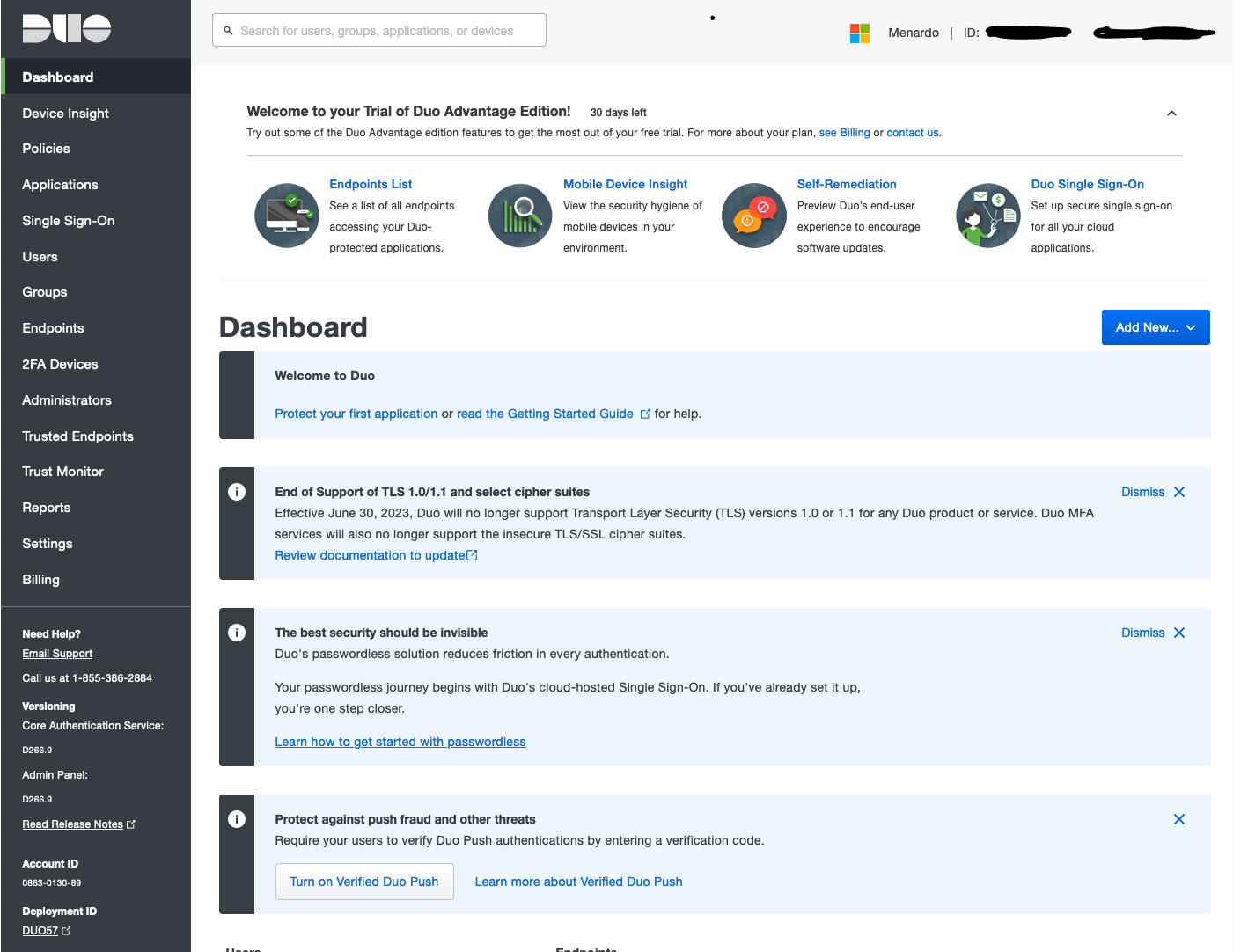
Licensing plan
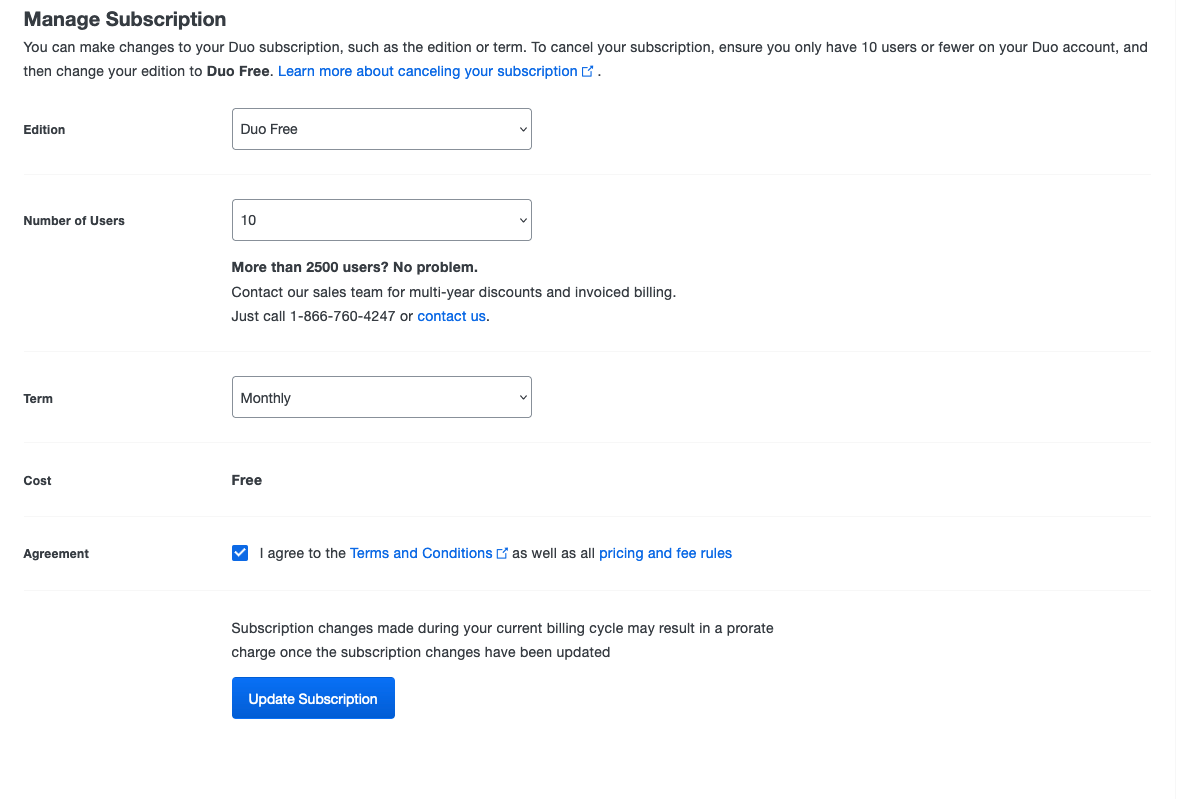
By default your account is created with a 30 days trial of an advanced license. Do whatever you want but I personnaly prefer to switch back to the Duo Free version. At least I know what feature I am sure to keep….
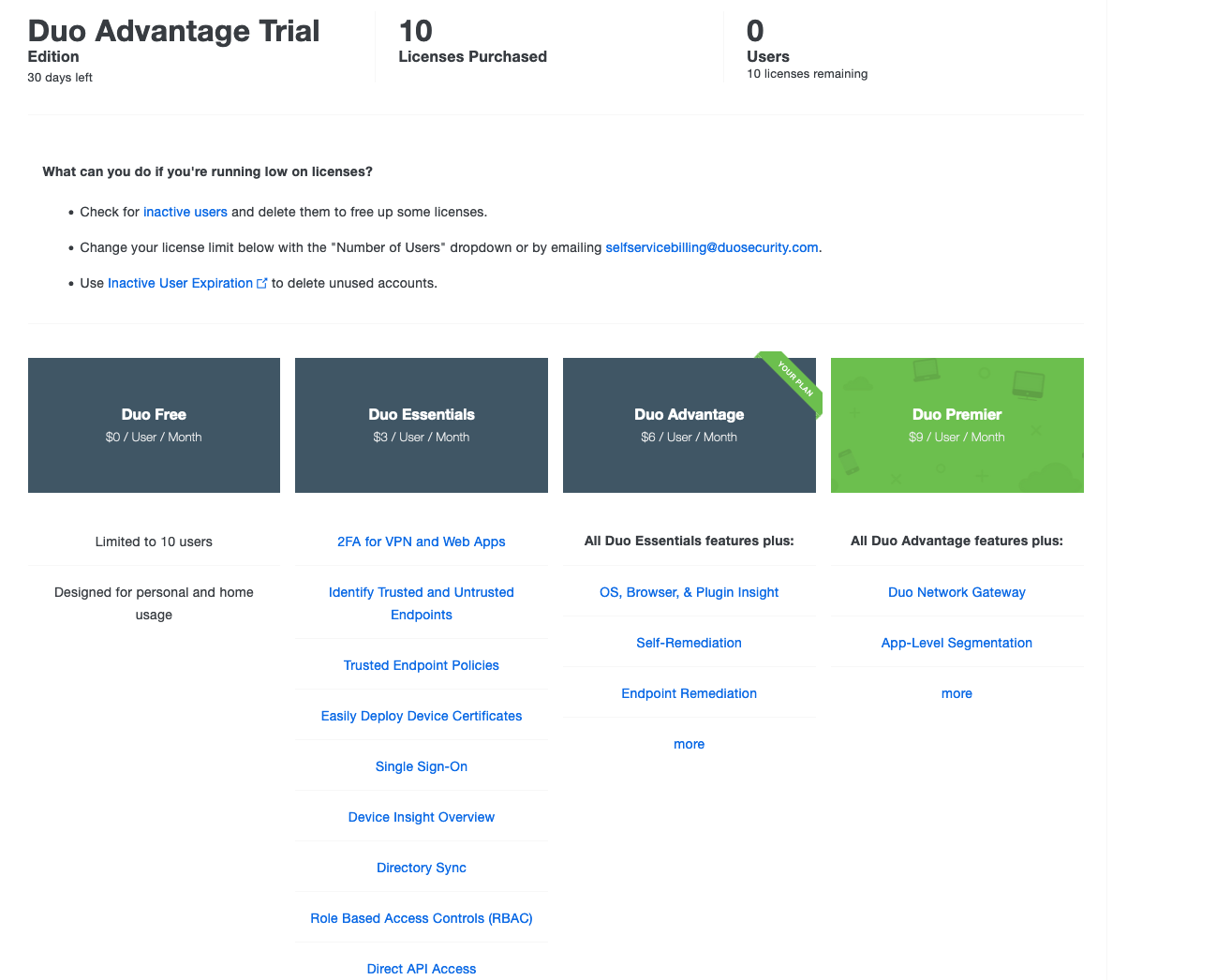
Lower in the billing page, you are able to configure it :
Policies
Basically there is two types of policies :
- A global policy : apply to all applications configured
- Custom policies : apply to a specific application
Due to the Free license, there is only one option configurable… the one that will define the action taken by duo when an unknown account is connecting to duo.
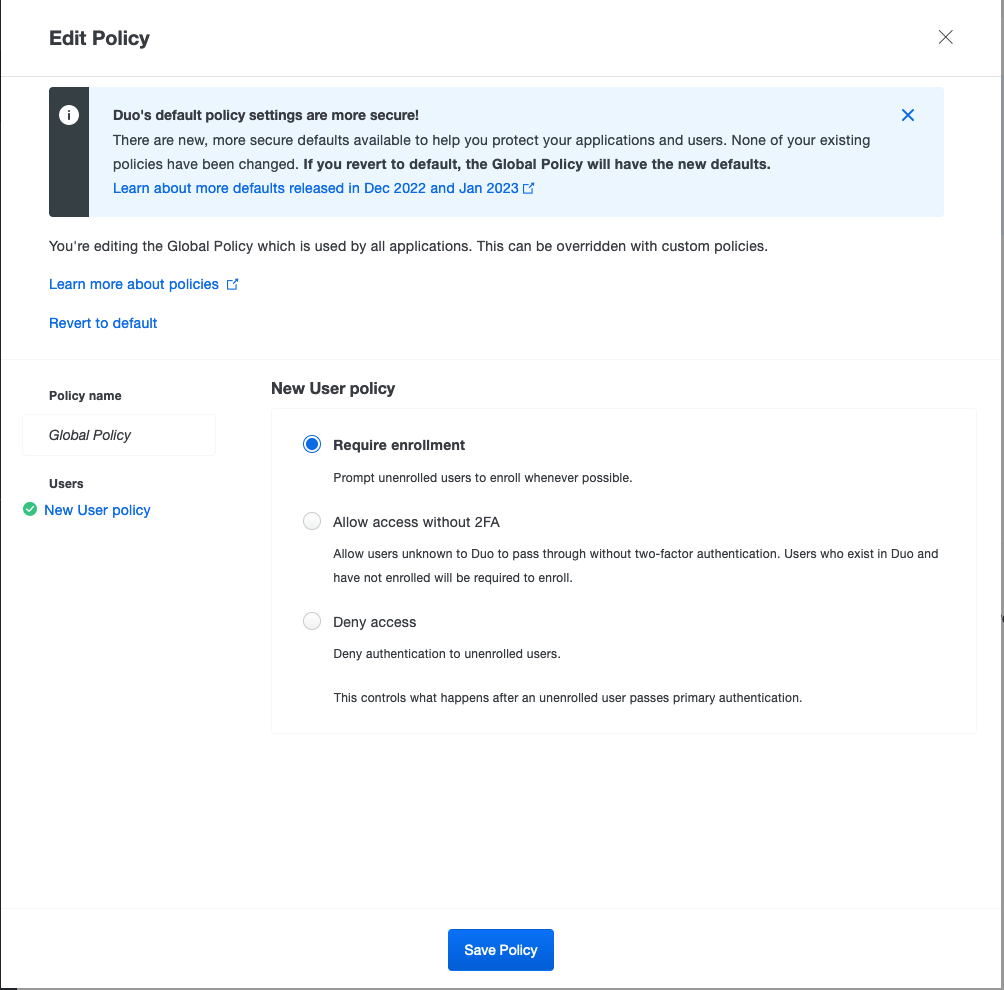
I will define a Global policy the set the Require enrollment in order that new users will begin automatically the onboarding process.
⚠️ If you do not want this behaviour, it’s possible to Deny access and enroll users manualy by creating the user account. An email will be automaticaly sent.
Depending on the type of application I will create a specific policy to overwrite this setting.
Invite your first user
Click on the Add user in the Users section
Define the username

Complete the information espcially the email adress used to send an enrollment email.
⚠️ If you username don’t match you linux username, you can add aliases in this form.
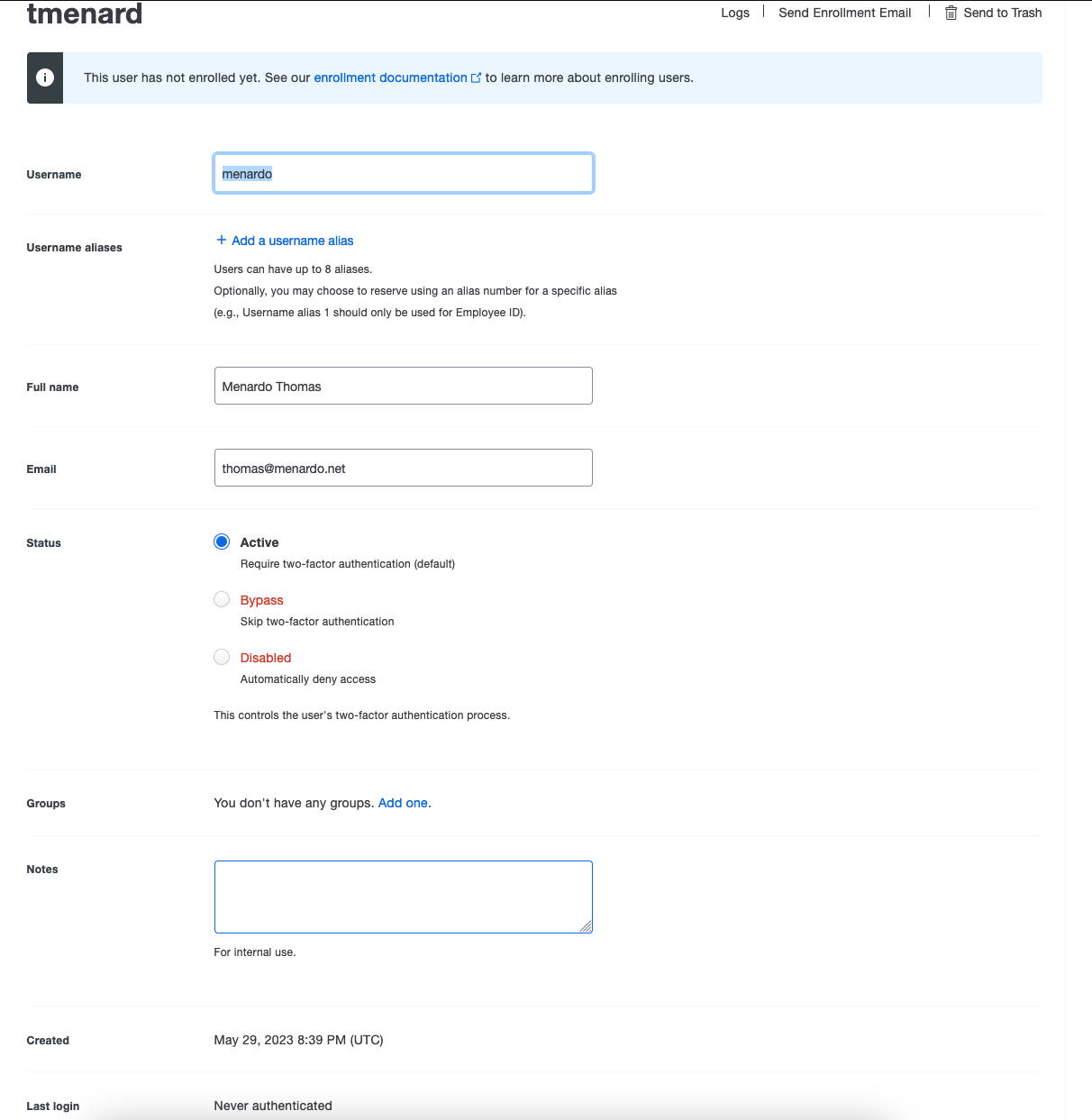
⚠️ If the user for any reason loose it’s second factor (even if you can enroll more than one second factor (Duo Mobile, FIDO2 key), it’s possible change the Status of the account to Bypass
You can now click on Send enrollment email in the user settings page.
The user will receive an email like this one:
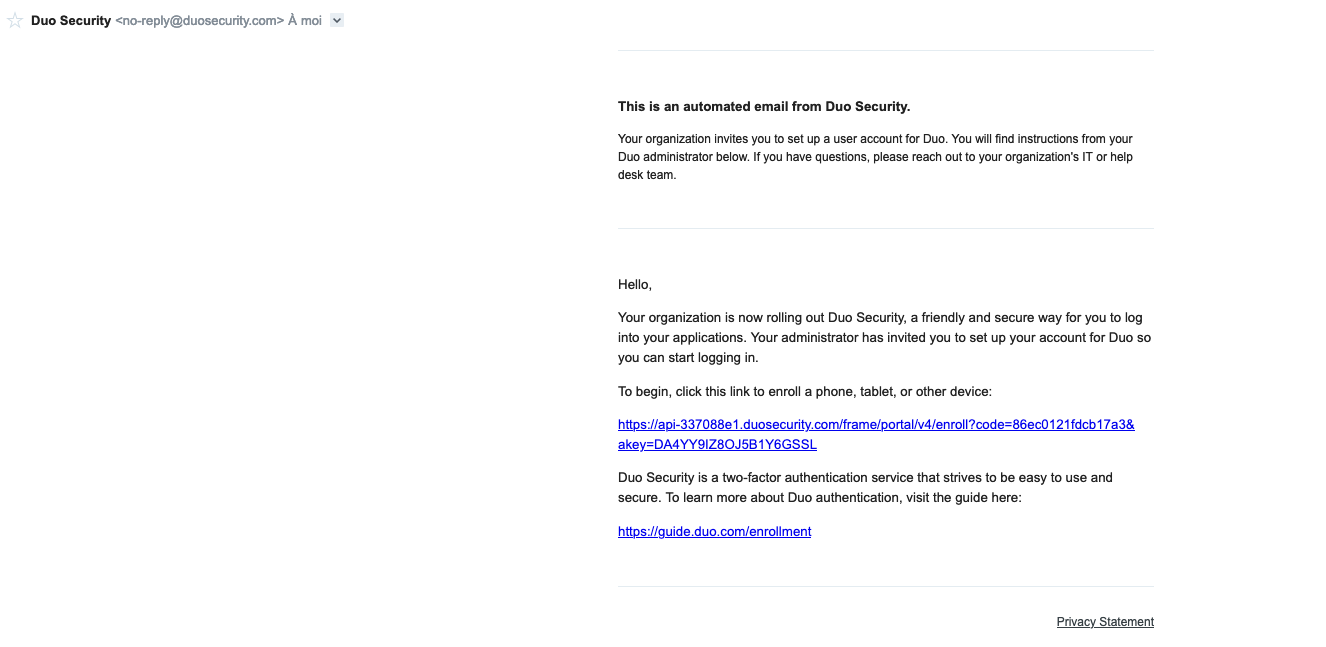
After clicking on the link the user is prompted to define is first second factor

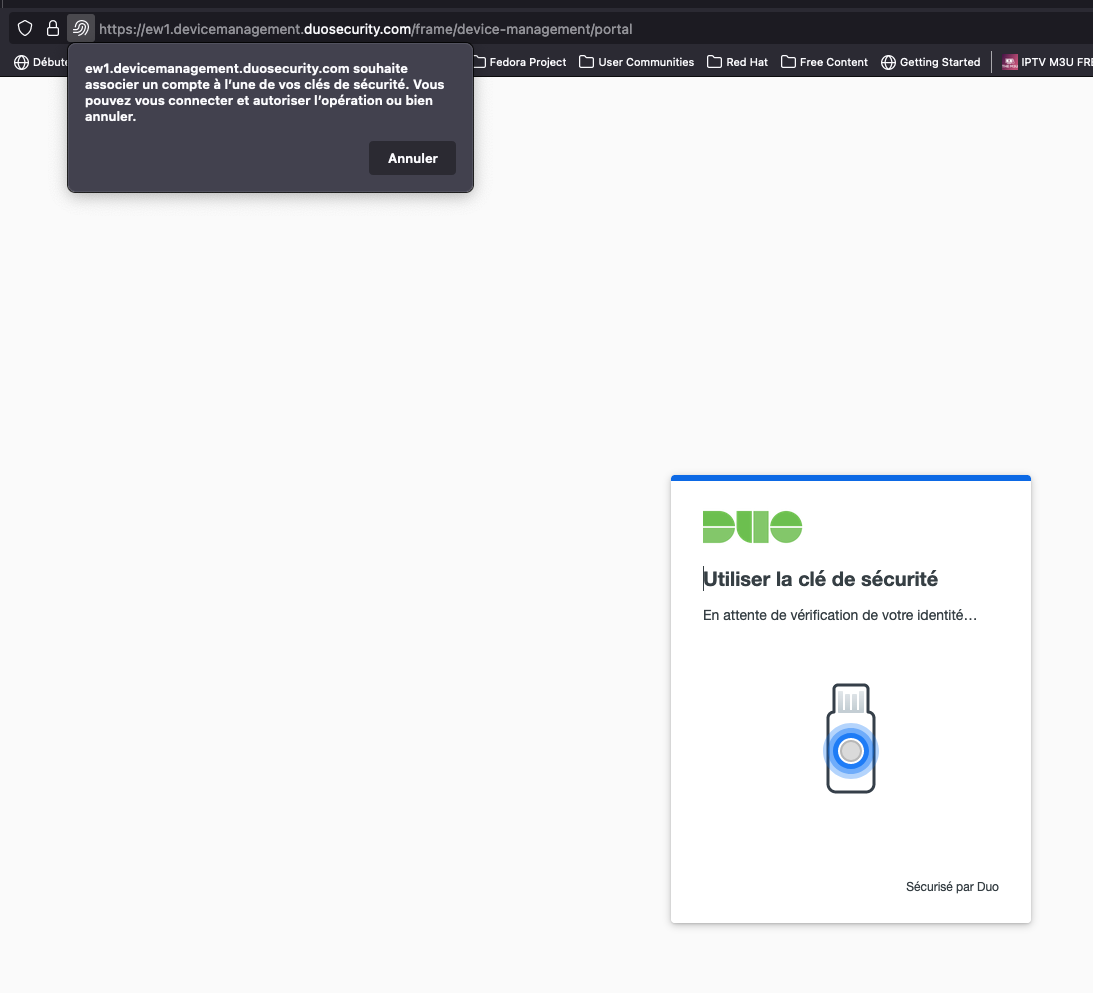
Choosing the Security key prompt you to insert your FIDO 2 key (here a Yubikey 5C)
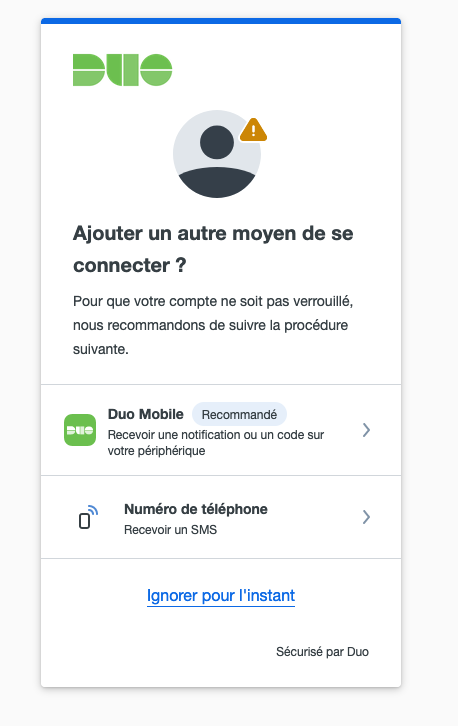
Next you may be prompted to enroll an aditionnal factor (just for security reason)
And you’re done with your first user.
