Learn how to secure an openssh server by adding Cisco DUO MFA.
When exposing an openssh server directly on internet remain an issue as plenty of robot will begin to scan you and try to connect, it’s always frightening to keep it open. Here we will implement Cisco DUO using a pam module in order to enforce the usage of a second factor.
First of all you need a Cisco account correctly configured.
Create the SSH application
On the Cisco Duo Admin panel, click on Protect an Application.
And search for UNIX Application, click on Protect

You will reach the following page describing the applications policies you can apply and the settings of the Global policy.
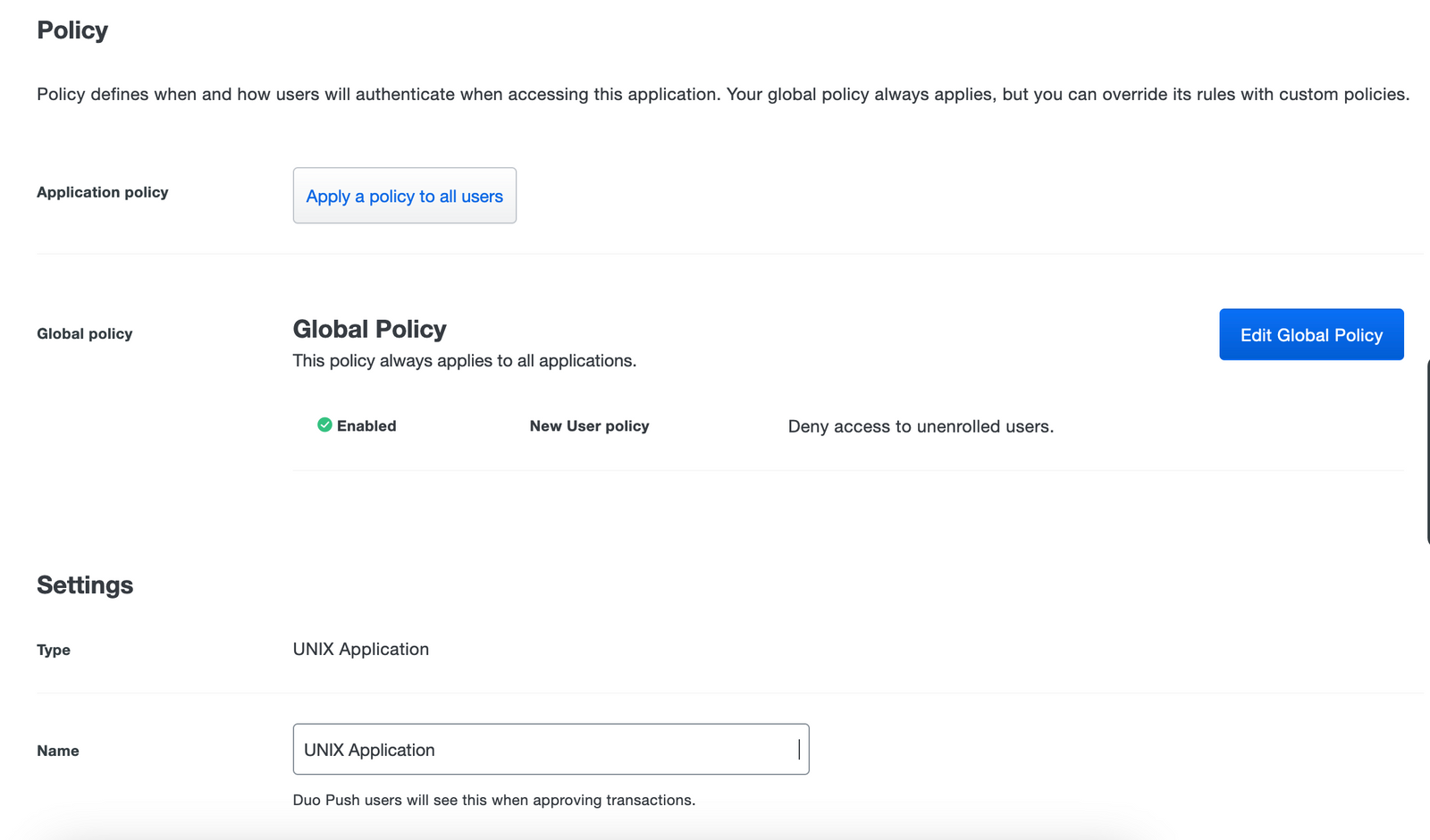
🤷 The Name field will be used in Duo Mobile when you get a popup to validate the second factor.
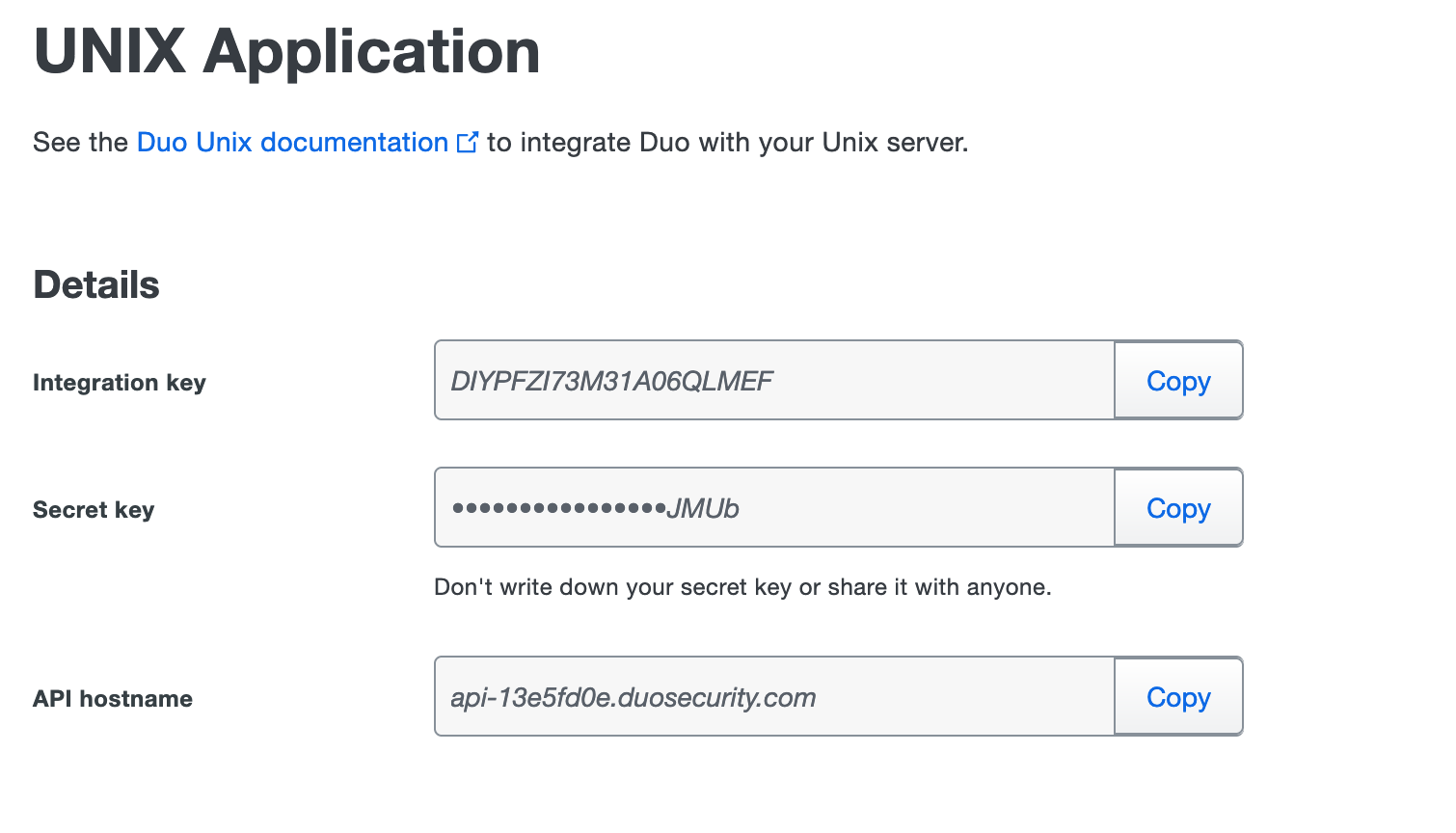
Once you have completed the settings, copy the credentials (top of the page)
Configure your server : pam_duo
🤷 Reference documentation : https://duo.com/docs/duounix
We are testing against a Rocky Linux 9 but the setup is basically the same on other distro.
Create /etc/yum.repos.d/duosecurity.repo
| |
Import the gpg key :
| |
The duo_unix package bundle 2 tools login_duo and pam_duo pam module.
We are going to implement the pam module as login_duo is for me less secure (configured in sshd and seems to be not so secure).
Edit the /etc/duo/pam_duo.conf and add the credentials you have copied before on the Duo Admin panel.
| |
🤷 You can extend the configuratiob file by adding a group settings where you can filter which group will get Duo Prompt
Now you will need to reconfigure your openssh server
⚠️ May 2023: As of now pam_duo support only one auth method at a time. You have to choose which auth method you want : publickey or password.
For this documentation I will use password authentication because for me publickey and Fido2 token or Duo Push are something you have factors… so it’s not enough for me.
🤮 Authentication using two or more factors to achieve authentication. Factors include: (i) something you know (e.g. password/personal identification number (PIN)); (ii) something you have (e.g., cryptographic identification device, token); or (iii) something you are (e.g., biometric).
Configure your server : sshd
To summarize the changes you will need to do, here is an extract of what is in the official documentation
| |
And for some newer system
| |
⚠️ On RHEL 9 based OS, there is an include file in /etc/ssh/sshd_config.d that you will use to put this modifications
| |
If you want to go a step further, you should block root connection (if needed you can log on root using the console…
In my case I modify the sshd_config with the following parameters
| |
And finaly restart the ssh server
| |
Configure your server : pam ssh
Now we need to define the pam configuration for ssh logins
Edit /etc/pam.d/sshd (we will only focus on the auth section, don’t copy paste by replacing the whole file)
| |
Now you can try to start a new ssh session, you should get prompted for Duo auth after typing your password
| |
If you have enroll a FIDO2 key you can directly press the button on your key to generate the passphrase.
Configure your server : pam sudo
If you want to go a step further and want to also secure sudo command, you can alter your pam configuration in /etc/pam.d/system-auth.
| |
🤷 duo_unix unfortunately don’t use the latest improvement of the latest Redhat based distro aka authselect. You like it or hate it, anyway the thing is that system-auth pam configuration is a link to an authselect profile. Altering like this is not bad … it’s just dirty. Maybe in the future it will be implemented.
