Background
As an IT Geek, I like to test stuff at home… adding multiple apps during my spare time is sadly funny for me….
Having access from the outside for example when going to work (because I want to be sure my new toy is useful for me -:) ) is sometime necessary.
Some apps are OIDC or SAML compliant and some are not… having a centralized authentication server is mandatory for me (as an IT Guy…).
As my homelab is only composed of a single synology NAS (a DS1520+) resource consumption is something to take in consideration.
At first I gave a try with Authelia which is great once you passed the configuration step but lack of functionality. You can use OIDC for supported applications, it have MFA support and can be connected to Cisco DUO. The memory footprint is ridiculous (30MB of RAM in my memories), for my use case it fits completely.
One of the drawback is like old identity provider (like shibboleth for example); as it is yaml config based, each time you add an application you need to restart and be sure that you don’t have configuration errors. Proxying non oidc native applications is still possible using third party apps (Nginx Proxy Manager, Traefik…) but lack of credential injection. Accounts have to be stored on a file db or an ldap server (ok I have ldap on synology…).
The main advantages of Authentik :
- More agile in the development cycle
- Built in account management
- Proxy mode
- LDAP and Radius Endpoint
- Look and Feel
- Customization
Looking at the system prerequisites found on Authentik documentation, it seems that this will not fit on my NAS…
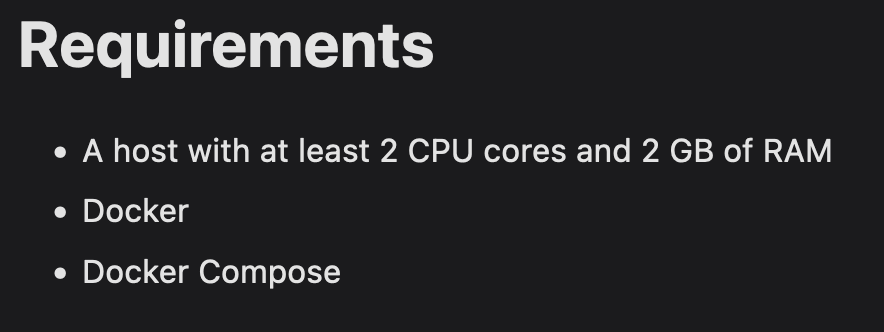 In the doubt I wanted to give it a try as we are not going to be a lot if users… maybe it will not consume that much.
In the doubt I wanted to give it a try as we are not going to be a lot if users… maybe it will not consume that much.
Authentik deployment
Looking at the documentation of the deployment using docker-compose the docker-compose look like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
|
---
version: "3.4"
services:
postgresql:
image: docker.io/library/postgres:12-alpine
restart: unless-stopped
healthcheck:
test: ["CMD-SHELL", "pg_isready -d $${POSTGRES_DB} -U $${POSTGRES_USER}"]
start_period: 20s
interval: 30s
retries: 5
timeout: 5s
volumes:
- database:/var/lib/postgresql/data
environment:
POSTGRES_PASSWORD: ${PG_PASS:?database password required}
POSTGRES_USER: ${PG_USER:-authentik}
POSTGRES_DB: ${PG_DB:-authentik}
env_file:
- .env
redis:
image: docker.io/library/redis:alpine
command: --save 60 1 --loglevel warning
restart: unless-stopped
healthcheck:
test: ["CMD-SHELL", "redis-cli ping | grep PONG"]
start_period: 20s
interval: 30s
retries: 5
timeout: 3s
volumes:
- redis:/data
server:
image: ${AUTHENTIK_IMAGE:-ghcr.io/goauthentik/server}:${AUTHENTIK_TAG:-2023.5.1}
restart: unless-stopped
command: server
environment:
AUTHENTIK_REDIS__HOST: redis
AUTHENTIK_POSTGRESQL__HOST: postgresql
AUTHENTIK_POSTGRESQL__USER: ${PG_USER:-authentik}
AUTHENTIK_POSTGRESQL__NAME: ${PG_DB:-authentik}
AUTHENTIK_POSTGRESQL__PASSWORD: ${PG_PASS}
volumes:
- ./media:/media
- ./custom-templates:/templates
env_file:
- .env
ports:
- "${COMPOSE_PORT_HTTP:-9000}:9000"
- "${COMPOSE_PORT_HTTPS:-9443}:9443"
worker:
image: ${AUTHENTIK_IMAGE:-ghcr.io/goauthentik/server}:${AUTHENTIK_TAG:-2023.5.1}
restart: unless-stopped
command: worker
environment:
AUTHENTIK_REDIS__HOST: redis
AUTHENTIK_POSTGRESQL__HOST: postgresql
AUTHENTIK_POSTGRESQL__USER: ${PG_USER:-authentik}
AUTHENTIK_POSTGRESQL__NAME: ${PG_DB:-authentik}
AUTHENTIK_POSTGRESQL__PASSWORD: ${PG_PASS}
# `user: root` and the docker socket volume are optional.
# See more for the docker socket integration here:
# https://goauthentik.io/docs/outposts/integrations/docker
# Removing `user: root` also prevents the worker from fixing the permissions
# on the mounted folders, so when removing this make sure the folders have the correct UID/GID
# (1000:1000 by default)
user: root
volumes:
- /var/run/docker.sock:/var/run/docker.sock
- ./media:/media
- ./certs:/certs
- ./custom-templates:/templates
env_file:
- .env
volumes:
database:
driver: local
redis:
driver: local
|
We are going to customize it a little bit to fit our needs on a Synology NAS (note that I use portainer to schedule container stack).
Basically I have a dedicated share on my NAS where I store all the data of my containers. This is mostly due to backup concern and make it more easy to maintain (edit various config files without having to enter in the container).
So lets say that my root directory on my nas is /volumes1/docker/authentik
1
2
|
mkdir -p /volumes1/docker/authentik/{database,redis}
mkdir -p /volumes1/docker/authentik/app/{media,certs,custom-templates}
|
And now update the docker-compose.yaml like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
|
---
version: "3.4"
services:
postgresql:
image: docker.io/library/postgres:12-alpine
restart: unless-stopped
healthcheck:
test: ["CMD-SHELL", "pg_isready -d $${POSTGRES_DB} -U $${POSTGRES_USER}"]
start_period: 20s
interval: 30s
retries: 5
timeout: 5s
volumes:
- /volumes1/docker/authentik/database:/var/lib/postgresql/data
environment:
POSTGRES_PASSWORD: ${PG_PASS:?database password required}
POSTGRES_USER: ${PG_USER:-authentik}
POSTGRES_DB: ${PG_DB:-authentik}
env_file:
- .env
redis:
image: docker.io/library/redis:alpine
command: --save 60 1 --loglevel warning
restart: unless-stopped
healthcheck:
test: ["CMD-SHELL", "redis-cli ping | grep PONG"]
start_period: 20s
interval: 30s
retries: 5
timeout: 3s
volumes:
- /volumes1/docker/authentik/redis:/data
server:
image: ${AUTHENTIK_IMAGE:-ghcr.io/goauthentik/server}:${AUTHENTIK_TAG:-2023.5.1}
restart: unless-stopped
command: server
environment:
AUTHENTIK_REDIS__HOST: redis
AUTHENTIK_POSTGRESQL__HOST: postgresql
AUTHENTIK_POSTGRESQL__USER: ${PG_USER:-authentik}
AUTHENTIK_POSTGRESQL__NAME: ${PG_DB:-authentik}
AUTHENTIK_POSTGRESQL__PASSWORD: ${PG_PASS}
volumes:
- /volumes1/docker/authentik/app/media:/media
- /volumes1/docker/authentik/app/custom-templates:/templates
env_file:
- .env
ports:
- "${COMPOSE_PORT_HTTP:-9000}:9000"
- "${COMPOSE_PORT_HTTPS:-9443}:9443"
worker:
image: ${AUTHENTIK_IMAGE:-ghcr.io/goauthentik/server}:${AUTHENTIK_TAG:-2023.5.1}
restart: unless-stopped
command: worker
environment:
AUTHENTIK_REDIS__HOST: redis
AUTHENTIK_POSTGRESQL__HOST: postgresql
AUTHENTIK_POSTGRESQL__USER: ${PG_USER:-authentik}
AUTHENTIK_POSTGRESQL__NAME: ${PG_DB:-authentik}
AUTHENTIK_POSTGRESQL__PASSWORD: ${PG_PASS}
# `user: root` and the docker socket volume are optional.
# See more for the docker socket integration here:
# https://goauthentik.io/docs/outposts/integrations/docker
# Removing `user: root` also prevents the worker from fixing the permissions
# on the mounted folders, so when removing this make sure the folders have the correct UID/GID
# (1000:1000 by default)
user: root
volumes:
- /var/run/docker.sock:/var/run/docker.sock
- /volumes1/docker/authentik/app/media:/media
- /volumes1/docker/authentik/app/certs:/certs
- /volumes1/docker/authentik/app/custom-templates:/templates
env_file:
- .env
|
Now we need to create the .env file
1
2
3
4
5
6
7
8
9
10
11
12
13
|
COMPOSE_PORT_HTTP=10080 # bind port on the host for http
COMPOSE_PORT_HTTPS=10443 # bind port on the host for https
PG_PASS=<password>
AUTHENTIK_SECRET_KEY=<secret key>
AUTHENTIK_TAG=2023.5.1
AUTHENTIK_EMAIL__HOST=smtp-mail.outlook.com
AUTHENTIK_EMAIL__PORT=587
AUTHENTIK_EMAIL__USERNAME=TBD
AUTHENTIK_EMAIL__PASSWORD=TBD
AUTHENTIK_EMAIL__USE_TLS=true
AUTHENTIK_EMAIL__USE_SSL=false
AUTHENTIK_EMAIL__TIMEOUT=10
AUTHENTIK_EMAIL__FROM=TBD
|
For password the install documentation is well done, pwgen is very usefull. If you are not using linux, you can use a password generator.
1
2
3
4
|
echo "PG_PASS=$(pwgen -s 40 1)" >> .env
echo "AUTHENTIK_SECRET_KEY=$(pwgen -s 50 1)" >> .env
# Because of a PostgreSQL limitation, only passwords up to 99 chars are supported
# See https://www.postgresql.org/message-id/[email protected]
|
Normaly you are good to go and you should be able to start it using:
1
2
3
4
5
6
7
8
9
10
11
|
$ docker compose up -d
[+] Running 32/32
⠿ worker Pulled
⠿ postgresql Pulled
⠿ server Pulled
[+] Running 5/5
⠿ Network authentik_default Created 0.1s
⠿ Container authentik-redis-1 Started 1.4s
⠿ Container authentik-worker-1 Started 1.4s
⠿ Container authentik-postgresql-1 Started 1.1s
⠿ Container authentik-server-1 Started
|
You should be able to access to the Authentik web interface https://:10443/if/flow/initial-setup in order to create the admin account.
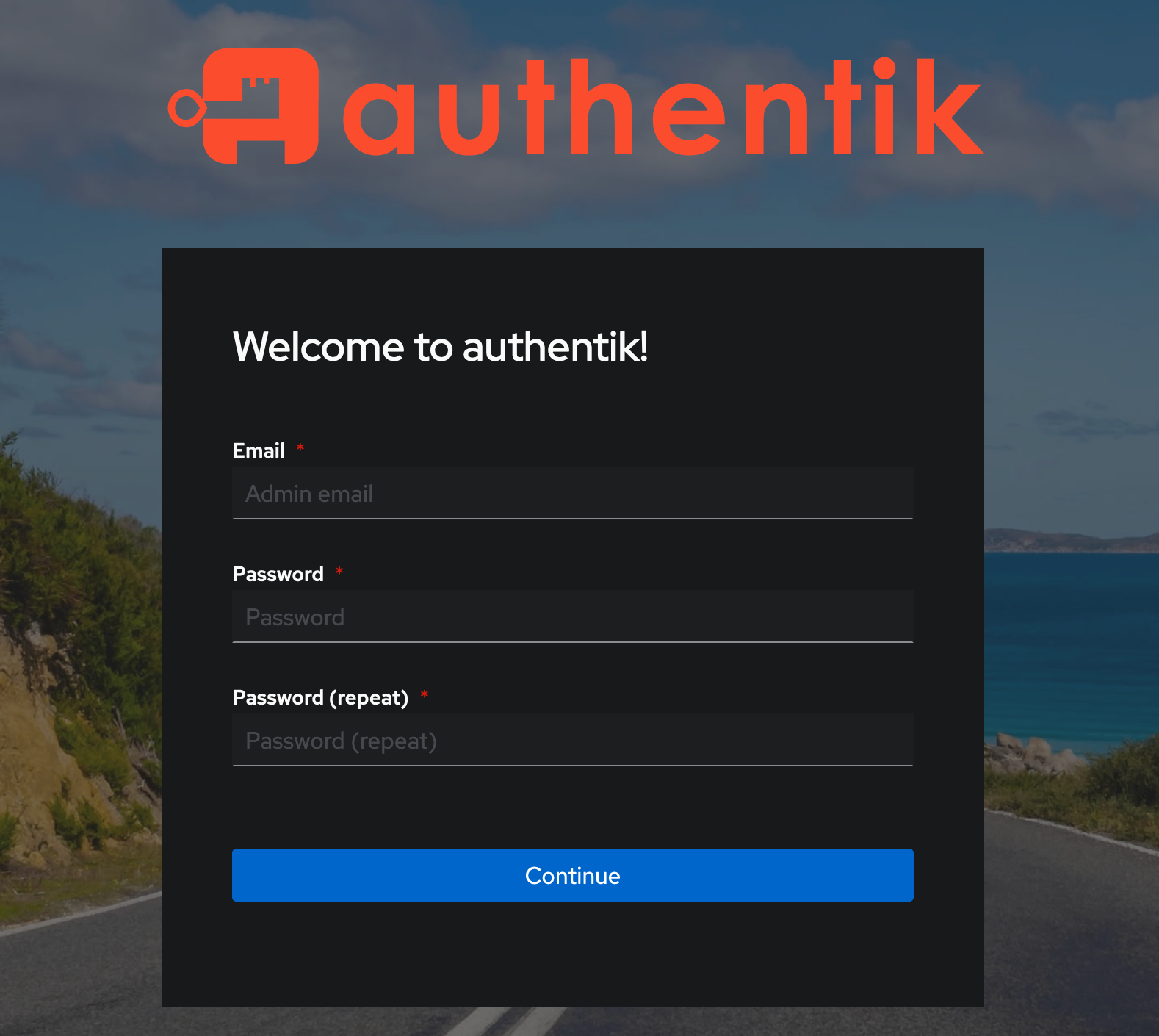
 In the doubt I wanted to give it a try as we are not going to be a lot if users… maybe it will not consume that much.
In the doubt I wanted to give it a try as we are not going to be a lot if users… maybe it will not consume that much.
